Try Hack Me/Brains
Write-up / THM / Brains
Start the Virtual Machine
Run an nmap scan to the VM machine
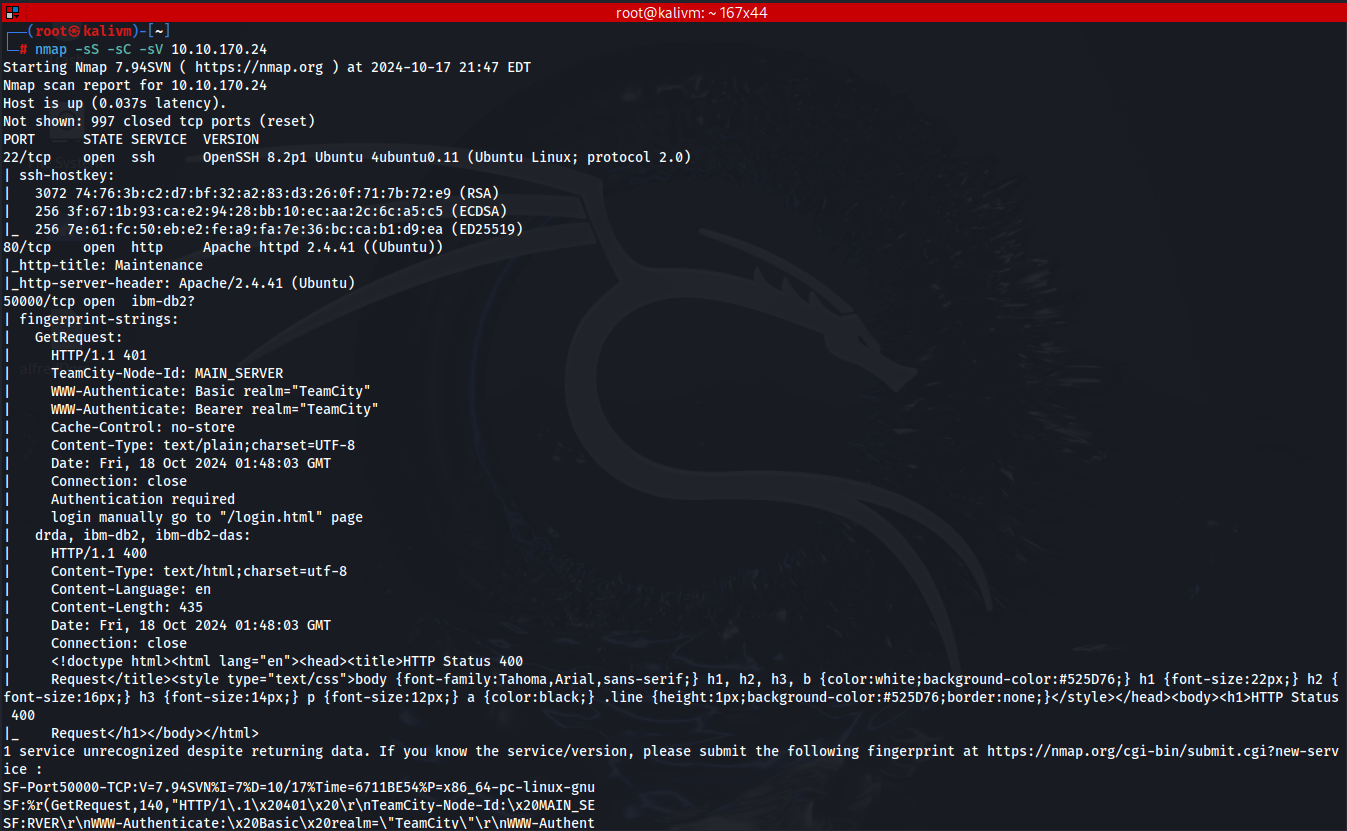
From the nmap scan: nmap -sS -sC -sV IP_THM_VM_machine
Ports 22, 80, and 50000 are open
VM machine is an Ubuntu Linux
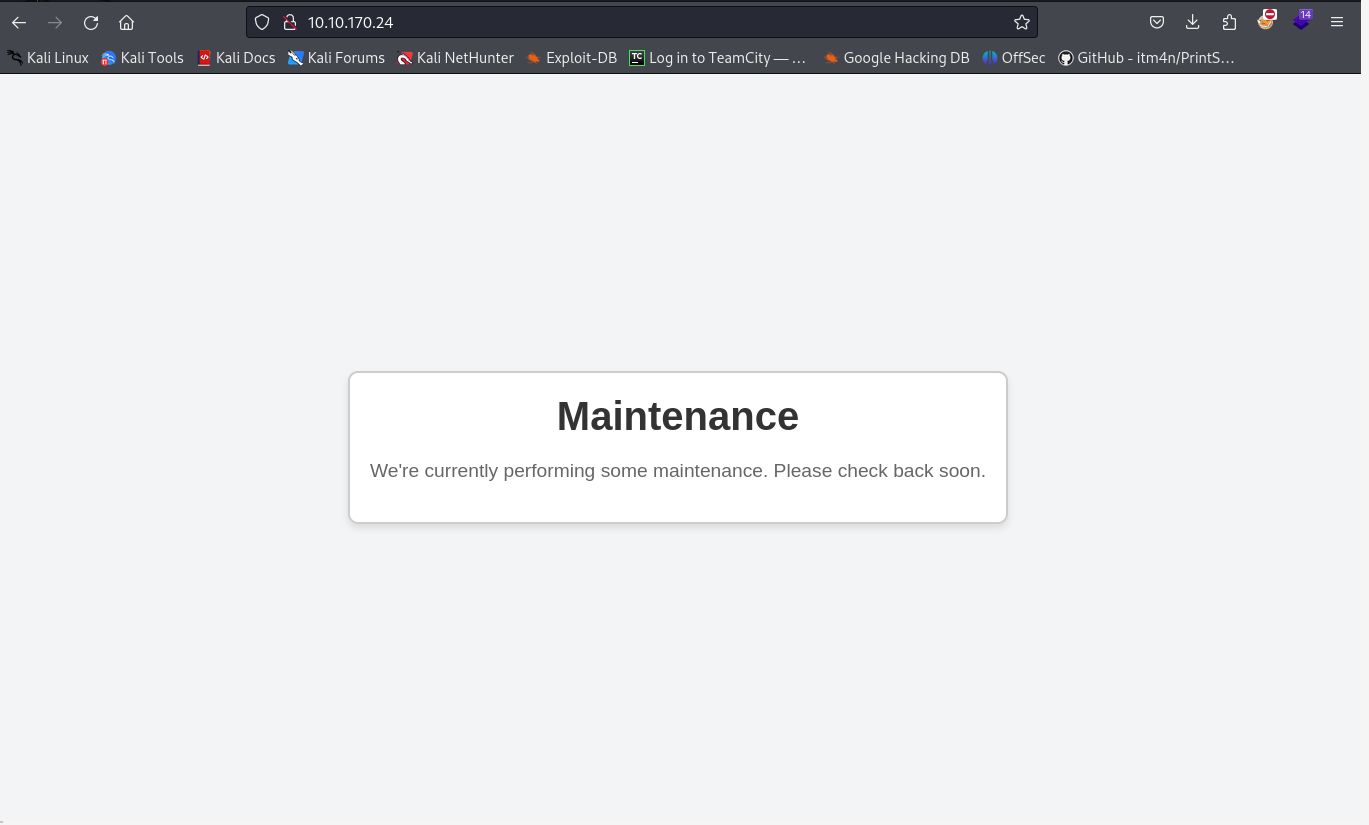
Connect to port 80 using a web browser
In the result of the nmap, port 50000 is also open and observing the result it is an http server
50000/tcp open ibm-db2?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 401
| TeamCity-Node-Id: MAIN_SERVER
| WWW-Authenticate: Basic realm="TeamCity"
| WWW-Authenticate: Bearer realm="TeamCity"
| Cache-Control: no-store
| Content-Type: text/plain;charset=UTF-8
| Date: Fri, 18 Oct 2024 01:48:03 GMT
| Connection: close
| Authentication required
| login manually go to "/login.html" page
| drda, ibm-db2, ibm-db2-das:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Fri, 18 Oct 2024 01:48:03 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
TeamCity-Node-Id: MAIN_SERVER
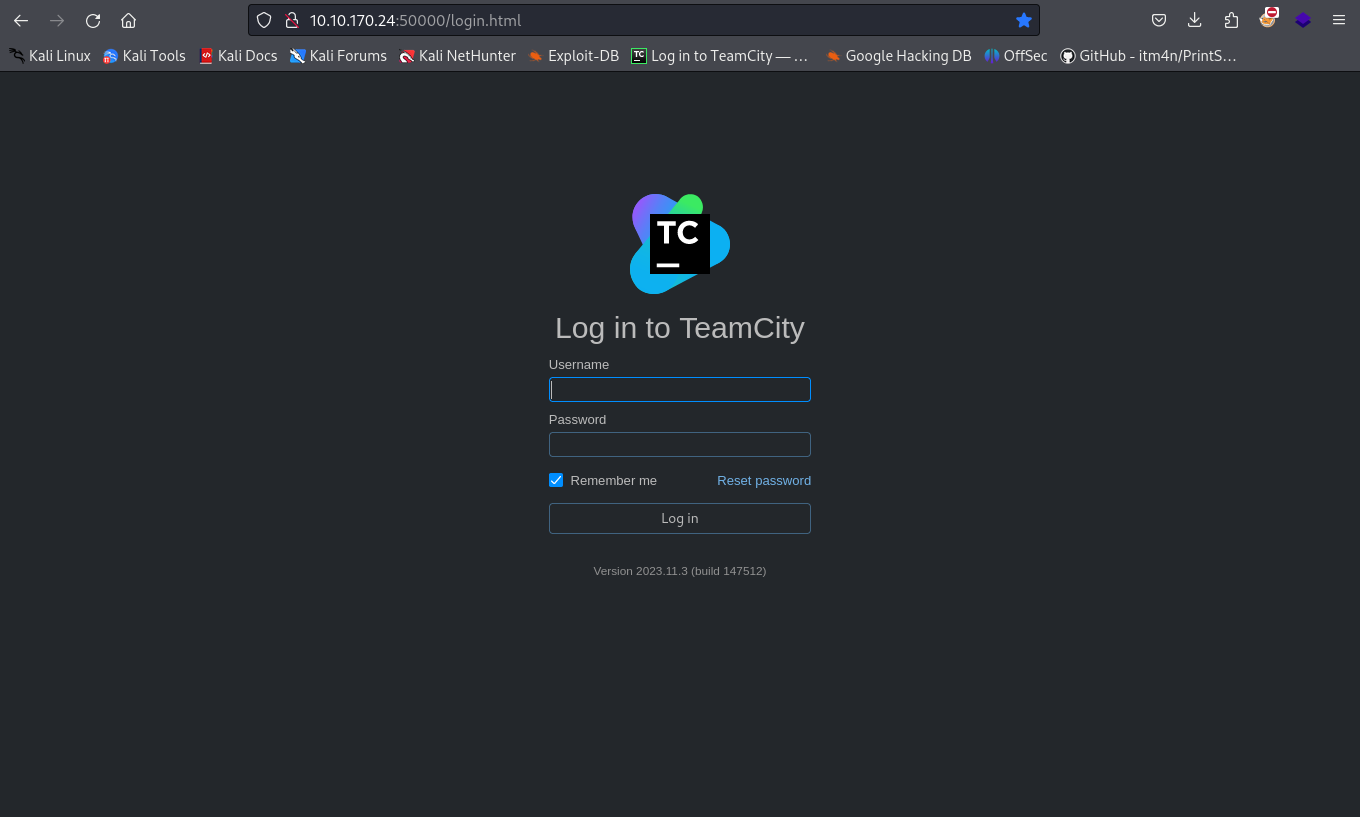
Connect to port 50000 using the web browser
The webserver has an application of Teamcity Version 2023.11.3 (build 147512)
Search the vulnerability of the Teamcity version 2023.11.3